LinkDaddy Cloud Services: Key Technologies and Newest Growths
LinkDaddy Cloud Services: Key Technologies and Newest Growths
Blog Article
Achieve Service Continuity With Secure Cloud Storage Space Services
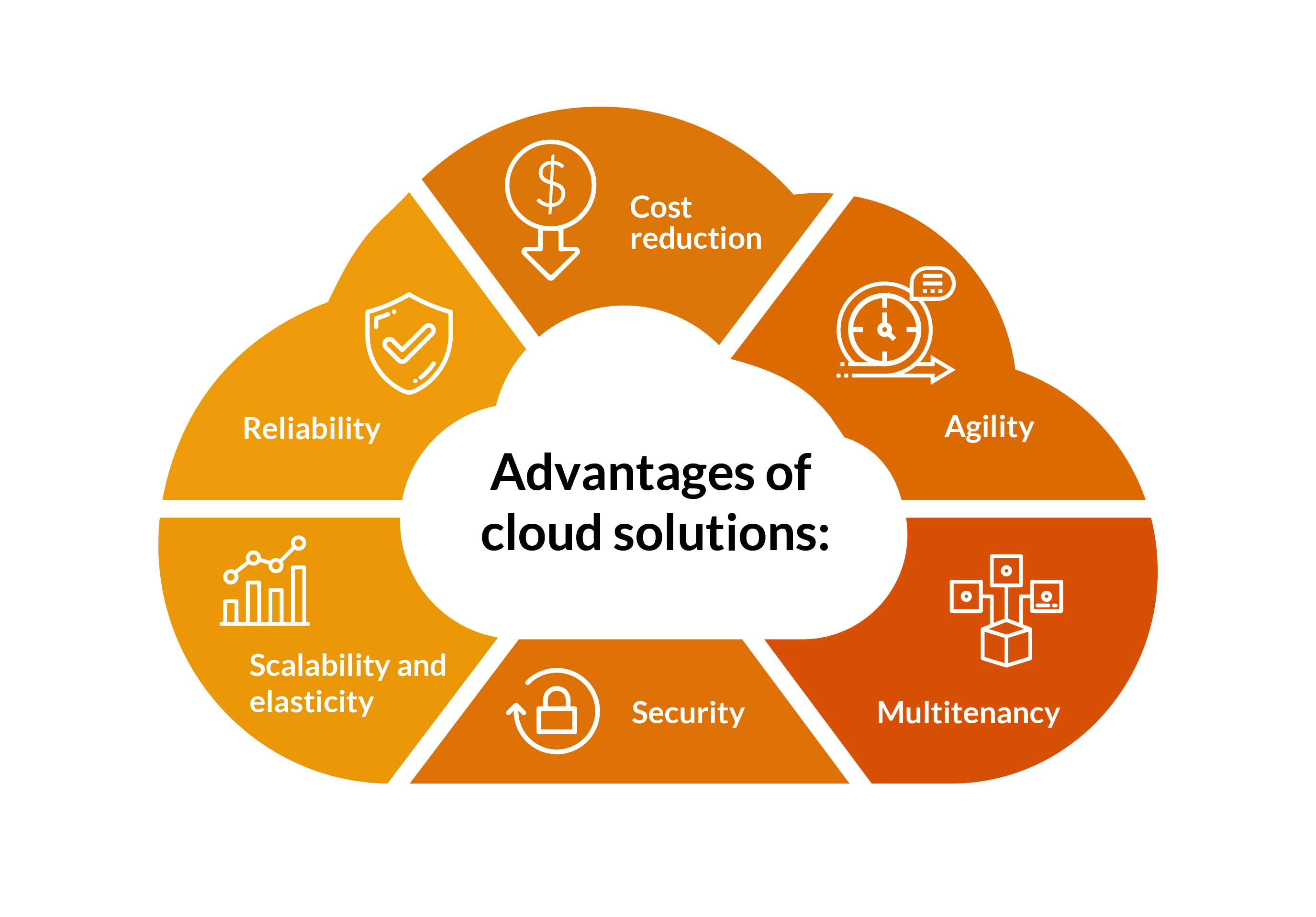
Advantages of Secure Cloud Storage
Undoubtedly, protected cloud storage space uses companies a multitude of advantages in terms of information defense and access. By saving data on trustworthy cloud systems that use encryption and innovative safety procedures, organizations can guard their information from unapproved access or cyber risks. Generally, the benefits of secure cloud storage space convert into improved data administration, boosted functional performance, and enhanced protection for businesses of all dimensions.
Trick Functions for Service Connection

In addition, one more essential attribute for organization continuity is redundancy. Redundancy involves having several copies of information kept in various locations to stop a single factor of failing (linkdaddy cloud services press release). By dispersing information across numerous servers or information centers, organizations can mitigate the threat of data loss and make sure continuous accessibility to their info. Generally, these vital functions collaborate to form an extensive business connection method that safeguards important data and operations.
Importance of Data Security
In today's interconnected electronic landscape, securing delicate details is paramount, making the relevance of information file encryption a basic facet of preserving data stability and protection. Information file encryption involves encoding info in such a means that only licensed parties can access and understand it. By converting information right into a safe and secure layout, encryption works as a guard versus unauthorized access, minimizing the threat of information violations and cyber threats.

Disaster Recuperation Approaches
A robust calamity recuperation strategy includes describing treatments to recover data, applications, and IT facilities in the event of a disaster. One essential aspect of a reliable strategy is normal information backups. By storing data in safe and secure cloud storage services, organizations can ensure that important info is protected and quickly accessible in instance of a calamity.
Picking the Right Service Supplier
To make sure smooth company continuity and effective disaster recuperation, selecting a trusted and ideal service company for protected cloud storage space is extremely important. Guarantee they employ durable encryption approaches, have rigid accessibility controls, and comply with market guidelines to guard your data. In addition, evaluate the copyright's information recovery capabilities.
Moreover, think about the scalability and versatility of the cloud storage solution. Your service needs might evolve with time, so it's necessary to pick a supplier that can suit your expanding storage demands and adapt to altering conditions. Analyze the service provider's track document and credibility in the sector. Try to find reviews, testimonies, and study to evaluate their dependability and performance. By carefully reviewing these variables, you can select a cloud storage company that straightens with your business's demands and makes sure constant operations in the face of potential disruptions.
Verdict
To conclude, go to these guys safe and secure cloud storage solutions use important benefits for accomplishing organization continuity, including improved safety attributes, smooth scalability, efficient cooperation devices, durable information back-up devices, and disaster recuperation strategies. Data security plays a crucial role in protecting sensitive information, while selecting the best solution company is key to ensuring conformity with laws and maintaining functional efficiency. universal cloud Service. Safe cloud storage is a useful possession in today's electronic landscape for making sure uninterrupted company operations
Data backup mechanisms are crucial for safeguarding versus data loss due to system official statement failings, cyber-attacks, or human mistakes. By dispersing data throughout various web servers or data centers, organizations can reduce the danger of data loss and ensure continual accessibility to their info.In today's interconnected electronic landscape, protecting delicate information is critical, making the importance of information file encryption a fundamental facet of maintaining data honesty and security. By transforming information right into a safe layout, security acts as a shield versus unauthorized gain access to, minimizing the risk of data violations and cyber hazards.
Conformity needs and information security policies often mandate the use of encryption to secure delicate info, stressing its crucial duty in modern-day data safety and security techniques.
Report this page